Oauth2 Proxy是一个反向代理,支持提供基于如谷歌、Azure、OpenID Connect和许多身份提供者的认证服务,也可以和dex一起使用。
介绍
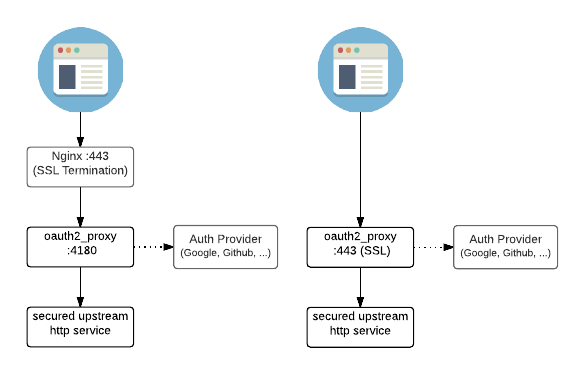
oauth2-proxy 本质是一个反向代理服务器,有两种使用方式:
- 把服务放到 oauth2-proxy 后面
- 在 nginx 后放 oauth2-proxy 通过它来代理到需要认证的服务
支持的认证后端
- Google(default)
- Azure
- ADFS
- Facebook
- GitHub
- GitLab
- 等
使用场景
- 为没有登录验证的服务提供认证服务,比如prometheus,skywalking等
使用
启动服务
http_address="0.0.0.0:4180"
# openssl rand -base64 32 | tr -- '+/' '-_'
cookie_secret="soEgqyyPwyKNBImOCaVtCVslhnfD7eIQcfOQ7zyQKvA="
provider="github"
email_domains="gmail.com"
client_id="xxx"
client_secret="xxx"
scope = "user:email"
reverse_proxy=true
cookie_secure="false"
cookie_domains=".xiexianbin.cn"
whitelist_domains=".xiexianbin.cn"
version: '3.0'
services:
oauth2-proxy:
image: quay.io/oauth2-proxy/oauth2-proxy:v7.2.1
command: --config /oauth2-proxy.cfg
ports:
- 4180:4180
volumes:
- "./oauth2-proxy-nginx.cfg:/oauth2-proxy.cfg"
restart: always
docker-compose up
nginx 代理实现
nginx 编译时需要支持 --with-http_auth_request_module
server {
listen 443 ssl;
server_name ...;
include ssl/ssl.conf;
location /oauth2/ {
proxy_pass http://127.0.0.1:4180;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Scheme $scheme;
proxy_set_header X-Auth-Request-Redirect $request_uri;
# or, if you are handling multiple domains:
# proxy_set_header X-Auth-Request-Redirect $scheme://$host$request_uri;
}
location = /oauth2/auth {
proxy_pass http://127.0.0.1:4180;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Scheme $scheme;
# nginx auth_request includes headers but not body
proxy_set_header Content-Length "";
proxy_pass_request_body off;
}
location / {
auth_request /oauth2/auth;
error_page 401 = /oauth2/sign_in;
# pass information via X-User and X-Email headers to backend,
# requires running with --set-xauthrequest flag
auth_request_set $user $upstream_http_x_auth_request_user;
auth_request_set $email $upstream_http_x_auth_request_email;
proxy_set_header X-User $user;
proxy_set_header X-Email $email;
# if you enabled --pass-access-token, this will pass the token to the backend
auth_request_set $token $upstream_http_x_auth_request_access_token;
proxy_set_header X-Access-Token $token;
# if you enabled --cookie-refresh, this is needed for it to work with auth_request
auth_request_set $auth_cookie $upstream_http_set_cookie;
add_header Set-Cookie $auth_cookie;
# When using the --set-authorization-header flag, some provider's cookies can exceed the 4kb
# limit and so the OAuth2 Proxy splits these into multiple parts.
# Nginx normally only copies the first `Set-Cookie` header from the auth_request to the response,
# so if your cookies are larger than 4kb, you will need to extract additional cookies manually.
auth_request_set $auth_cookie_name_upstream_1 $upstream_cookie_auth_cookie_name_1;
# Extract the Cookie attributes from the first Set-Cookie header and append them
# to the second part ($upstream_cookie_* variables only contain the raw cookie content)
if ($auth_cookie ~* "(; .*)") {
set $auth_cookie_name_0 $auth_cookie;
set $auth_cookie_name_1 "auth_cookie_name_1=$auth_cookie_name_upstream_1$1";
}
# Send both Set-Cookie headers now if there was a second part
if ($auth_cookie_name_upstream_1) {
add_header Set-Cookie $auth_cookie_name_0;
add_header Set-Cookie $auth_cookie_name_1;
}
proxy_pass http://backend/;
# or "root /path/to/site;" or "fastcgi_pass ..." etc
}
}